- Products
- Use Cases
- Process contractors and validate credentials
- Improve facility compliance to industry standards
- Improve speed of visitor check-in process
- Screen visitors or restrict access to my facility
- Automate my reception experience
- Improve and automate my facility evacuation process
- Manage facility security across multiple locations
- Industries
- Pricing
- Resources
- Company
Last week, our team ventured into the heart of the security world at the GSX - Global Security Exchange event in Dallas. This gathering brought together security professionals, experts, and enthusiasts from across North America. From all the chatter and insights, we've pinpointed the top concerns and needs shaping the security landscape.
Top Security Concerns from GSX 2023

1. Lagging Technological Advancements
One thing we kept hearing over and over was how folks felt that security tech just isn't keeping up with the times. The rise of drones, for instance, presents a unique challenge. Traditional security measures might be effective at addressing ground-level threats, but drones can bypass these by accessing open spaces. This highlights the need for a more holistic approach to security, where both ground and aerial threats are considered.

Moreover, the rise of the Internet of Things (IoT) has expanded the potential attack surface for cybercriminals. As homes and businesses integrate more connected devices, from smart thermostats to security cameras, the potential attack surface for cybercriminals expands. Each device, if not properly secured, can become a gateway for unauthorized access or data breaches.
2. Data Management and Compliance
At our booth, one topic kept coming up again and again: the challenges of data management, especially in light of new regulations popping up worldwide. In today's digital age, managing data isn't just about gathering it. It's about making sure it's stored safely, handled right, and stays in line with a constantly changing set of global rules. For instance, the General Data Protection Regulation (GDPR) in the European Union mandates strict guidelines on data collection, storage, and processing. Non-compliance can result in hefty fines, not to mention the reputational damage.
Similarly, the California Consumer Privacy Act (CCPA) in the U.S. gives consumers more control over their personal data, requiring businesses to be transparent about their data practices. With such regulations in place, security professionals are constantly navigating the tightrope of ensuring robust data practices while adhering to regional and global standards.
3. Active Threats and Emergency Preparedness
The topic of active shooters and the pressing need for effective emergency evacuations loomed large in discussions. In today's world, the importance of being able to swiftly account for every individual—whether an employee, visitor, or contractor—during emergencies cannot be overstated.
Beyond the immediate physical threat, the psychological ramifications of such events are profound. Fear of potential threats can erode trust within an organization. Employees who are constantly anxious or fearful are less likely to collaborate openly, share ideas, or engage in team activities. This atmosphere of distrust and apprehension can significantly hamper productivity. Moreover, the constant undercurrent of fear can lead to increased absenteeism, higher turnover rates, and overall decreased job satisfaction.
For businesses, this underscores the dual responsibility of ensuring physical safety while also fostering a sense of security and trust among employees. A comprehensive security strategy isn't just about reacting to threats, but proactively creating an environment where employees feel safe, valued, and confident in their organization's commitment to their well-being.
The Top 3 Pain Points in the Security Sector
1. Compliance with Contractors
Ensuring contractors adhere to security protocols is a nuanced challenge. With contractors often moving between various sites and projects, maintaining a consistent security protocol can be daunting. Their transient nature can lead to lapses in security, especially if each visit requires a reiteration of safety protocols, permissions, and access controls.
2. Managing Large-Scale Visitor Access
Balancing the welcoming of genuine visitors with the enforcement of stringent security measures is no small feat. Especially when overseeing large groups, maintaining a real-time log of everyone on-site becomes a logistical challenge. The risk is that in trying to simplify access, security could be compromised, and vice versa.
3. Disjointed System Integration
The frustration of having multiple, non-synchronized systems on a single site was evident. In an era where integration is key, the lack of seamless communication between systems can pose significant operational challenges, especially when swift data sharing and response times are crucial.

The Fix: Leveraging a Facility & Visitor Management Platform
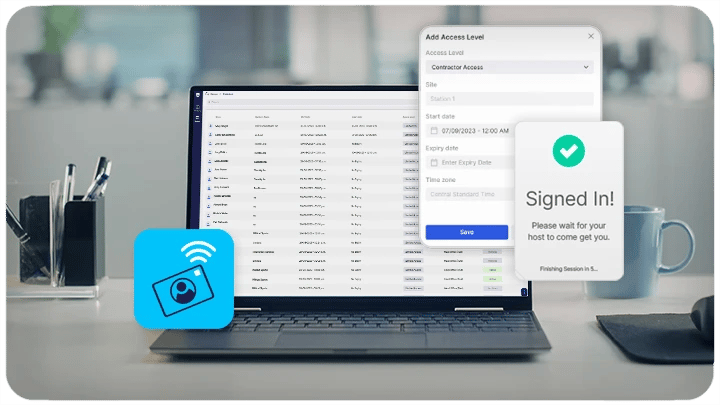
A Facility & Visitor Management Platform can solve for the aforementioned pains. Here's how:
- Pre-registration: Before a contractor or visitor even arrives on-site, they can be pre-registered in the system. This not only speeds up the contractor sign-in process but also ensures that all necessary background checks or verifications are completed in advance.
- E-signed Safety Documents: Instead of relying on physical paperwork that can be lost or overlooked, a dedicated platform can facilitate e-signing of safety documents. Contractors and visitors can review and sign necessary safety protocols and compliance documents digitally, ensuring that they are always up-to-date with the latest regulations and site-specific requirements.
- Access Control Integration: With a facility management platform, individuals can be granted specific access permissions tailored to their tasks. This ensures they can access only the areas they need, reducing potential security risks.
- Real-time Monitoring and Alerts: Addressing the challenge of overseeing large groups, a system can offer real-time monitoring of visitors, ensuring that security personnel are always aware of who is on-site. Instant alerts can be sent out for any unauthorized access attempts or security breaches.
- Seamless System Synchronization: To combat the issue of disjointed system integration, modern platforms are designed to seamlessly integrate with other security and operational systems. This ensures a unified approach to security, where data flows smoothly between systems, enhancing response times and operational efficiency.
By integrating a Facility & Visitor Management Platform, organizations can navigate the complexities of contractor compliance, large-scale visitor management, and system integration, ensuring a safer and more streamlined operational environment.
Proactive Solutions for Today's Security Challenges

GSX 2023 provided a comprehensive look into the challenges and needs of today's security professionals. As the landscape continues to evolve, the importance of adaptability, integration, and a proactive approach cannot be overstated. For those seeking to address these challenges, iLobby delivers impactful solutions that support a safer and more secure workplace.
iLobby
iLobby is the global leader in facility and visitor management for complex enterprises and regulated industries. Deployed across more than 6,000 sites worldwide, iLobby’s FacilityOS platform powers complex work environments by optimizing and automating key facility processes to achieve regulatory compliance, enforce safety protocols, and drive site security requirements.
Related Posts
View All Posts
Security
3 min read
Unpacking Insights from Safety23: Key Takeaways from This Year’s Conference
Continue Reading
Visitor Management
3 min read
2023 Market Report: Visitor & Emergency Management
Continue Reading
Security
5 min read
