- Products
- Use Cases
- Process contractors and validate credentials
- Improve facility compliance to industry standards
- Improve speed of visitor check-in process
- Screen visitors or restrict access to my facility
- Automate my reception experience
- Improve and automate my facility evacuation process
- Manage facility security across multiple locations
- Industries
- Pricing
- Resources
- Company
How to Optimize Enterprise Visitor Access Control
February 8, 2023
Return to work is in full swing. For many enterprise facilities and manufacturing plants, this doesn't mark a huge change for employees. However, visitors of all types - contractors, inspectors, interviewees, VIPs - have returned in droves.
Security officers are now often working with smaller teams or having to wear more hats. As a result, they desperately need more efficient solutions to manage visitor access, experience, and security.
Today, there is a need to integrate access control and visitor management systems to meet to satisfy security officers and facility managers.
This article discusses how enterprises get the most out of their visitor access systems.

Taking Control of Visitor Access in Enterprise Facilities
Visitor access control is crucial to maintaining the safety and security of both staff and guests. In many cases, it's also a key factor in protecting company assets. Visitor access control software features improve the ease and efficacy of managing facility permissions and controls, even by remote users.
A smart system improves all necessary controls
- Visitor sign in
- Multiple locations
- Multiple Entrances
- Gate control
- Security doors
- Turnstiles
Effective visitor management helps keep employees and assets safe while minimizing disruptions. Implementing a visitor management system will improve your office's safety and security.
-
Implement a Visitor Management System
A visitor management system records and tracks visitors in your facility. Gather and store information about your guests, such as their name and email or other contact information, their purpose for visiting your facility, length of their visit, time spent waiting in line or at the reception desk, and more.
You also have complete control over how long you keep personal visitor data. Preset, adjustable, and communicable data storage ease compliance and messaging.
The information collected through visitor management system access control software provides important insights to improve security and efficiency. The system automatically stores necessary data, making it possible to generate reports at the click of a button.
-
Maintain a Digital Guest Check-In Log
The days of having a physical log book with a visitor's name, phone number, and place they're visiting are over — or at least they should be. Digital visitor logs ease visitor data collection, storage, and permissions. With pre-registration, systems can even collect this information before visitors arrive.
Enabling advance visitor registration streamlines visitor sign-ins. Pre-registered guests can simply scan a QR to check in, providing all necessary data and avoiding long wait times or heavy lobby traffic. When scanning in at the visitor kiosk, digital guest registration kiosks can automatically print visitor badges on demand. Visitor badges offer many advantages, including enhanced security, speeding up return entries, and confirming identities.
Digital guest check-ins are also ideal for facility events. This process makes monitoring visitors at your event easier and identifies arrivals or missing people. Digital guest logs provide a more secure method of tracking visitors while onsite and help prevent unauthorized access to restricted areas throughout an event or conference. Best of all, guests check in through their smartphones instead of standing in line to physically check in.
-
Equip Building Security Personnel With Visitor Entry Notifications
More bodies aren't always better in security — the best security team isn't the biggest; it's the best equipped. Security officers and guards need the right tools to do their job effectively.
Visitor host notifications are one such tool. A visitor notification automatically sends to relevant parties when a guest signs into your facility. Notifications can alert visitor hosts, security officers, and other appropriate parties. In addition to keeping security personnel in the loop, this also ensures guests aren't waiting around, or hosts aren't surprised by arrivals. The result is a safer, more streamlined experience for everyone.
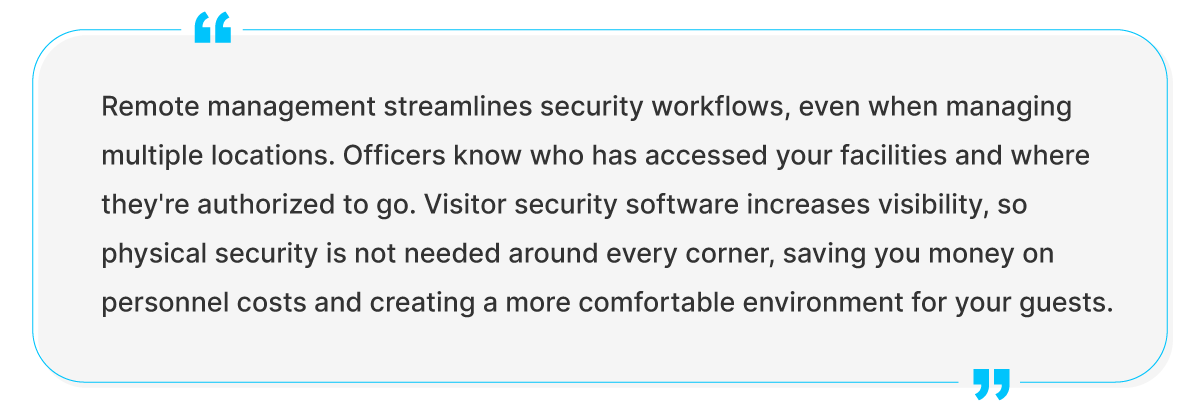
An access control platform also allows your security management to control doors and other facility access points remotely. Remote management streamlines security workflows, even when managing multiple locations. Officers know who has accessed your facilities and where they're authorized to go. Visitor security software increases visibility, so physical security is not needed around every corner, saving you money on personnel costs and creating a more comfortable environment for your guests.
-
Manage Facility Access Controls Remotely
Remote access is a transformative feature of an enterprise-level system because it allows security personnel to manage visitors across multiple locations and entry points easily. Security managers benefit from access control systems that provide remote management capabilities by monitoring activity and making changes or updates to the system without having to visit each location.
Additionally, remote access control allows your security staff to multitask and monitor multiple entries and exit points at one time while requiring fewer employees to do so.
-
Analyze Visitor Insights and Data
With a visitor access control system in place, you can track visitor data. This information gives actionable data to streamline your visitor management and facility security.

Visitor tracking systems provide valuable insights to optimize security and efficiency in your facility. Some insights include
- How many visitors enter per day
- The most active locations and entrances
- How long visitors stay
- Visitor types and purpose of visit
With systems in place to track your visitors, you will enjoy peace of mind from improved security and the ability to manage your building more effectively.
-
Integrate with Prominent Access Control Systems
Your visitor management software must integrate with your access control system.
This is important because it can help prevent liability by keeping unauthorized personnel out of regulated areas, such as sensitive facilities or patient rooms. It also ensures that guests only visit areas where they are allowed. Your employees don't waste time checking credentials repeatedly and ensuring everyone has the correct clearance throughout your facility.
Visitor management integrations can even incorporate denied party lists to enhance access control.
Smart VMS systems, like iLobby, already integrate with the most popular access control systems like:
- Honeywell
- Genetec
- Openpath
- Software House
- Brivo
Custom solutions are available for many other systems or when setting up a new access control solution.
The Access Control-Forward Visitor Management Solution
iLobby is synonymous with expertise and white-glove visitor management services. Our facility and visitor management software brings visitor access control into the 21st century.
We leverage technology and automation to reduce facility-related risk across organizations with multiple critical entry points. iLobby's access control and visitor management systems ease compliance with internal and regulatory standards and streamline your facility.
Schedule your demo today and discover the iLobby difference.


