- Products
- Use Cases
- Process contractors and validate credentials
- Improve facility compliance to industry standards
- Improve speed of visitor check-in process
- Screen visitors or restrict access to my facility
- Automate my reception experience
- Improve and automate my facility evacuation process
- Manage facility security across multiple locations
- Industries
- Pricing
- Resources
- Company
Physical Security Planning for Manufacturing & Facilities
November 14, 2022
As facilities become more technologically advanced, physical security has become an integral part of facility planning considerations. Physical security protects employees and property infrastructure from cybersecurity threats, unauthorized access, and compliance issues — making it more difficult for any illegitimate person to disrupt your facility operations. It creates a feeling of safety and security, improving productivity. Investing in physical security pays off in the long run, but there are some considerations you have to acknowledge while investing.
What Is Physical Security?
Physical security is the process of protecting people, property, and processes from harm. It includes measures to detect and respond to service disruptions caused by non-compliance, visitor mismanagement, emergencies, etc.
Physical security best practices aim to create a safe and secure work environment. The most effective approach targets specific site needs and is implemented through facility management platforms and security controls.
For example, an enterprise might use the records of audits and previous investigations to update security rules. By carefully assessing the risks and implementing appropriate physical security measures, businesses and organizations can significantly reduce the potential threats to their employees and assets.
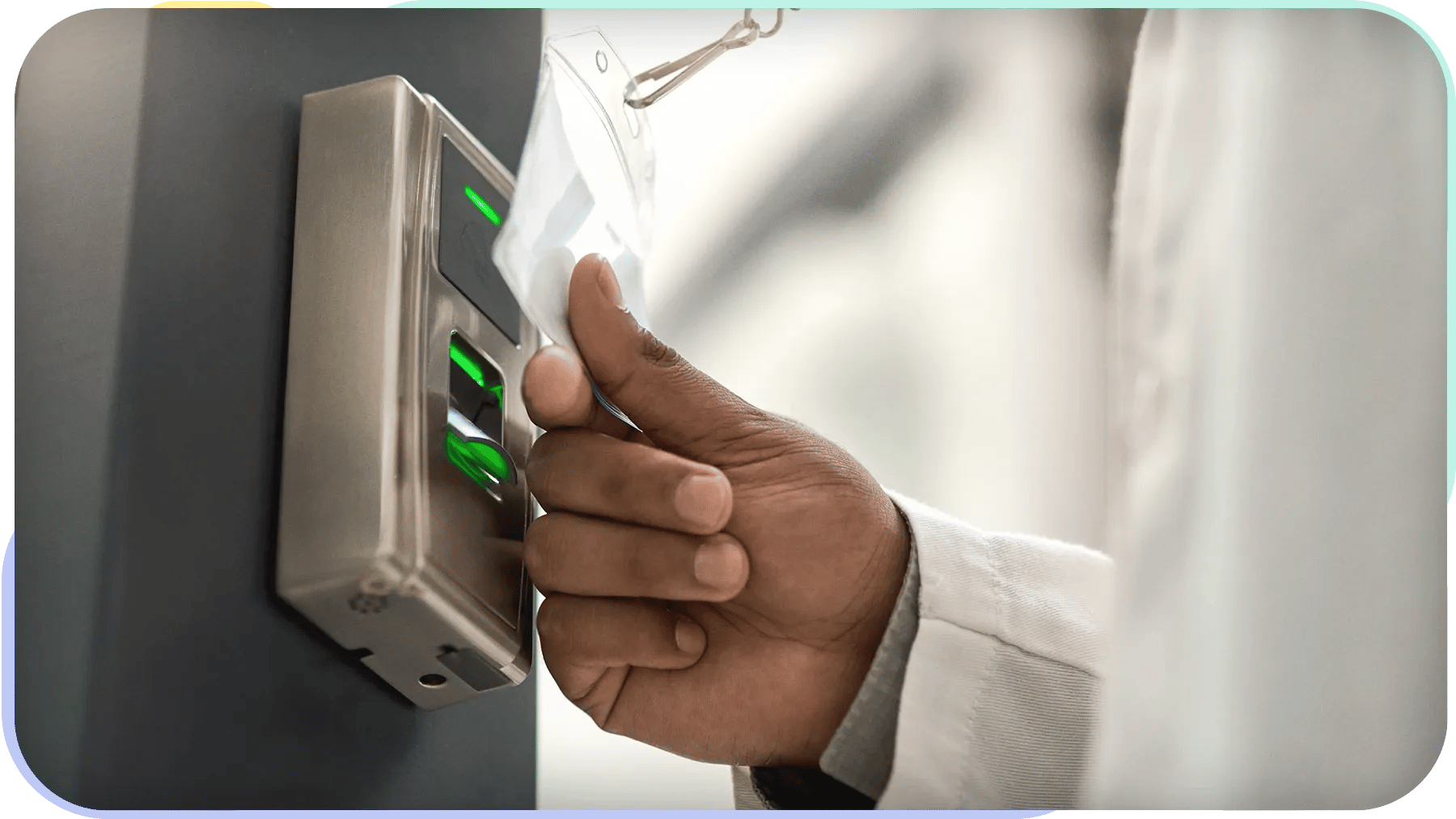
What Physical Security Measures Do Facilities Need?
There are several physical security measures that facilities should have in place to protect their employees, business assets, and classified information. These competent physical security policies and comprehensive assessments will help you protect your workplace from any security threat.
Technical Controls
Technical controls are an essential part of physical security guidelines. They help to detect unauthorized access, control entry points, and monitor activity. While they are not foolproof security measures, they can be an effective deterrent against theft, vandalism, and other crimes.
Technical controls include features like digital visitor logs, access cards, and visitor ID badges. When used in conjunction with other security measures, such as regular patrols and lighting, technical controls help create a more secure environment.
Access Controls
Access controls are a valuable component of technical security policies. Controlling physical access to your facility to:
Access controls can also help to prevent liability by keeping unauthorized personnel out of regulated areas.
In addition, access controls can improve the efficiency of security operations by eliminating the need for a team of security officers as well as decreasing the workload of the existing ones.
For reliable access control, iLobby integrates with your existing solutions and allows you to control all your facility management tasks using one cloud-based remote dashboard. Our Physical Identity & Access Management software enables you to automate access provisioning with rule-based workflows. This creates a safer and more secure environment for employees, customers, and visitors.
Visitor Tracking and Monitoring
Visitor tracking monitors the flow of visitors and employees in your facility and restricted areas. Using features like pre-registration, sign-in kiosks, digitized visitor logging, and ID badges provide a complete solution to visitor management. In short, physical security systems that include visitor tracking and monitoring can provide a high level of security for any building.
Physical Controls
Physical control is equally vital to physical security as much as technical controls. Most facilities are already using physical controls like security guards to protect the workplace, but they are often using outdated modes.
Physical controls' core focus should be the potential use of physical power and protection resources to lessen the security risks. And it should be done by carefully formulating practical security policies. The following guidelines serve to mitigate physical security threats proactively.
Perimeter Security
Perimeter security is an integral part of physical security policies. By detecting potential risks, they help to keep people and property safe. In many cases, perimeter security systems are the first line of defense against malicious intent. They can alert security personnel to external threats and may even be able to stop an intruder before they gain access to a building or area.
Intrusion Alarms
Intrusion alarms also work the same way as perimeter security and monitor sensitive areas or belongings, providing an extra layer of security. They identify the security threat on the spot.
Intrusion alarms use sensors and detect movement, like the opening of doors or windows on your property and produce alerts that notify the authorities, preventing the most significant damages.
How to Start Physical Security Planning
Physical security planning is achievable in any workplace using tried-and-tested strategies and software. You have to set up a strategy that characterizes all possible security threats and devise practical solutions.

Identify Minimum Security Standards
Identifying minimum security standards involves assessing the risks specific to the facility and determining what measures you must implement to mitigate those risks. For example, whether you need to implement screening, pre-registration, or demonstrations for visitors to secure your workplace.
For instance, a healthcare facility might screen candidates against certain medical conditions or tests. A defense industry exporter would screen against terrorist lists for ITAR compliance and government-issued lists of persons flagged for exporting issues or violations in the past. Similarly, a manufacturing facility might have to show video demonstrations to visitors for their safety or conduct safety quizzes during the induction flow.
Learn more about Visitor Management Systems for Factories & Manufacturing >
Conduct Risk Assessment Audits
Conducting a periodic risk assessment audit is critical to successful physical security planning. The audit helps to identify potential security vulnerabilities and recommend steps to mitigate them. Risk assessment audits identify gaps and dictate where to focus limited resources to make the most impact.
As such, audits are essential for organizations to maintain safety and security. For more information about security planning, read the workplace security best practices guide.
Streamline Your Facility Security
In today's world, security is more important than ever. With the rise of terrorist organizations and the ever-present threat of cybercrime, businesses and individuals must invest in technological systems to help streamline security.
For building a secure and safe workplace, book an iLobby demo today to discover how automation can minimize security risks and help you run your workplace smoothly.
Jeff Gladwish
Jeff Gladwish is the Chief Revenue Officer at iLobby where he spearheads the go-to-market strategy, driving the growth and adoption of our Facility and Visitor Management solutions. In 2023, Jeff was named one of Influitive’s Fearless 50 Customer-Led Marketing Leaders, an award that recognizes executives pushing the boundaries of customer marketing, advocacy, community, and loyalty.


